The file access method shown in Figure 12 is called ...
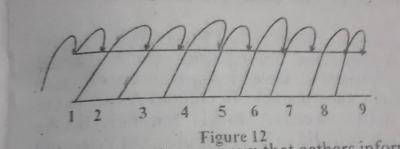
The file access method shown in Figure 12 is called
hashed access
indexed access
random access
sequential access
Correct answer is A
No explanation has been provided for this answer.
Similar Questions
Antivirus software is an example of? ...
The modifier keys on the computer keyboard comprises of? ...
The following actions are sources of breaches in computing except? ...
The ASCII chart control characters using numeric codes ranging from? ...
The following symbols are used in flowcharting except the? ...
Which of the following isn't used to navigate in a computer? ...
Fig.2 is a system development cycle. Use it to answer the question below The path label...
A Collection of software that allows the computer to operate is called? ...