The file access method illustrated in the diagram above i...
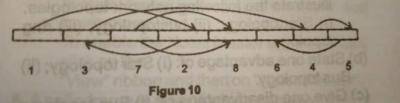
The file access method illustrated in the diagram above is called?
hashed access
indexed access
random access
sequential access
Correct answer is B
No explanation has been provided for this answer.
Similar Questions
Fig.2 is a system development cycle. Use it to answer the question below The path label...
Which of the following methods is not suitable for securing files? ...
The smallest unit of information representation which is addressable on the computer memory is? ...
The line segment that describes the contents of the message when sending an e-mail is? ...
Search engines are used for the following except? ...
Which of these application packages is mostly used by computer users? ...
The super computers are mainly used for ...
When the computer reboots itself without triggering the hardware based reset, it is called ? ...