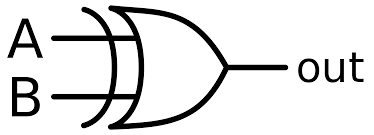
The logic gate in the figure above is
XNOR gate
NOT gate
XOR gate
OR gate
Correct answer is C
It's an XOR gate
denoted by Z = A ⊕ B.
A set of moral principles that regulate the use of computers is called
cyber security guidelines
computer ethics
computer safety laws
computer rules
Correct answer is B
Computer ethics is the term used to describe a set of moral principles that regulate the use of computers. It involves questions related to privacy, accuracy, property, and access
When records are given a new value, it is called
updation
insertion
deletion
retrieval
Correct answer is A
When records are given a new value, it is called 'updation'. This is a process in database management where an existing record is modified with new data. 'Insertion' is adding a new record, 'deletion' is removing a record, and 'retrieval' is fetching data from the database
Which of the following is used for modulation and demodulation ?
Gateway
Protocol
Modem
Multiplex
Correct answer is C
A modem(modulator-demodulator) is a hardware device that connects a computer or router to a broadband network
JAMB Subjects
Aptitude Tests