adware
time bomb
trojan horse
spyware
Correct answer is C
No explanation has been provided for this answer.
Which of the following options is not a similarity between computer file and manual file? Both can
be accessed
be retrieved
store multimedia
contain information
Correct answer is C
No explanation has been provided for this answer.
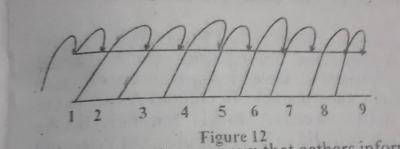
The file access method shown in Figure 12 is called
hashed access
indexed access
random access
sequential access
Correct answer is A
No explanation has been provided for this answer.
To prevent unforeseen data loss, a user must
edit the data
create the data
backup the data
defragment the data
Correct answer is C
No explanation has been provided for this answer.
The binary number 0.1101 in decimal is
0.8125
0.8215
0.8225
0.8512
Correct answer is C
No explanation has been provided for this answer.
WAEC Subjects
Aptitude Tests