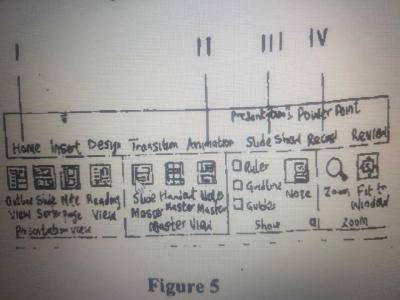
III
I
II
IV
Correct answer is C
The part used to apply motion effects to different objects of a slide in PowerPoint is "Animation". Animation effects in MS PowerPoint allow users to add movement, entrance, exit, and emphasis to individual objects on a slide. These effects help make presentation more dynamic and engaging.
People who use cathode ray tube monitor without antiglare screen are susceptible to
Blurred vision
Back ache
Repetitive strain injury
Stiffness of the wrist
Correct answer is A
People who use cathode ray tube (CRT) monitors without antiglare screens are susceptible to blurred vision. CRT monitors emit a significant amount of glare and can cause reflections on the screen due to ambient light sources. This glare and reflection can lead to visual discomfort, including blurred vision and eyestrain, when using the monitor for extended periods.
Antiglare screens or filters are used to reduce glare and reflections, making the screen easier to view and reducing the strain on the eyes. While CRT monitors are less common today, the issue of glare and visual discomfort is relevant to any type of screen, including modern LCD and LED displays.
Macromedia Dreamweaver application is used for
Surfing the internet
Graphic design
Intranet communication
Web design
Correct answer is D
Macromedia Dreamweaver (now part of Adobe Creative Cloud) is an application primarily used for web design. It's a professional web development tool that allows designers and developers to create, edit, and manage websites and web applications. Dreamweaver provides a visual interface for designing web pages and also offers coding capabilities for those who want to work with HTML, CSS, JavaScript, and other web technologies.
The application is not used for graphic design, intranet communication, or general internet browsing, as its main focus is on web development and design.
Artificial intelligence is a feature of
Fifth generation computers
Third generation computers
Second generation computers
Fourth generation computers
Correct answer is A
Artificial intelligence (AI) is a feature of fifth generation computers.
The first generation of computers were mainframe computers that used vacuum tubes. The second generation of computers used transistors, which were smaller and more efficient than vacuum tubes. The third generation of computers used integrated circuits (ICs), which allowed for even more compact and powerful computers. The fourth generation of computers used microprocessors, which are even smaller and more powerful than ICs.
Fifth generation computers are still in development, but they are expected to use artificial intelligence (AI) to perform tasks that are currently beyond the capabilities of human computers. For example, fifth generation computers could be used to translate languages, diagnose diseases, and write creative content.
The following precautionary measures are taken against virus infection except
Downloading e-mail and attachment before scanning it
Avoiding booting the computer with disks in it
Regular updating of antivirus
Avoiding the installation of piratted software
Correct answer is A
The precautionary measure downloading e-mail and attachment before scanning it is not taken against virus infection.
Here are some precautionary measures that can be taken against virus infection:
Regularly updating your antivirus software: This ensures that your antivirus software has the latest virus definitions to protect your computer from new viruses.
Avoiding opening suspicious e-mails and attachments: Many viruses are spread through e-mails and attachments. If you receive an e-mail from someone you don't know, or if the e-mail looks suspicious, don't open it.
Avoiding installing pirated software: Pirated software often contains viruses. If you don't want to get a virus, only install software from trusted sources.
Avoiding booting your computer with disks in it: If you boot your computer with a disk in it, the virus on the disk could infect your computer. Only boot your computer with disks from trusted sources.
It is important to note that no single precautionary measure can guarantee that your computer will not be infected with a virus. However, by taking all of these precautions, you can significantly reduce your risk of infection.
The precautionary measure of downloading e-mail and attachment before scanning it is not effective because viruses can be embedded in the e-mail or attachment itself. By downloading the e-mail or attachment, you are essentially giving the virus access to your computer.
It is better to scan the e-mail or attachment first before downloading it. If the scan finds a virus, you can delete the e-mail or attachment without putting your computer at risk.
WAEC Subjects
Aptitude Tests