The number of entries in the figure above is?
3
4
5
12
Correct answer is A
No explanation has been provided for this answer.
Ethical practice requires a computer user to
shutdown properly
hack into other peoples computer
intrude into peoples privacy
copy software without the license
Correct answer is A
No explanation has been provided for this answer.
Duplicating copyrighted electronic or digital content without the authors approval is considered?
felonious
ethical
treasonable
unethical
Correct answer is A
No explanation has been provided for this answer.
stored using a key
sorted in a particular order
stored as they come
stored in any storage media
Correct answer is C
No explanation has been provided for this answer.
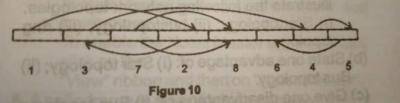
The file access method illustrated in the diagram above is called?
hashed access
indexed access
random access
sequential access
Correct answer is B
No explanation has been provided for this answer.
WAEC Subjects
Aptitude Tests